Few things are more frustrating for website owners and developers than seeing a browser display a “Not Secure” warning despite having a valid SSL certificate installed. These warnings can dissuade users, reduce trust, and even impact your SEO rankings. So, why does this issue occur if you’ve already secured your site with SSL? The answer lies in a series of common misconfigurations and hidden pitfalls that can sneak past even seasoned administrators.
Understanding the “Site Not Secure” Warning
When you see “Not Secure” in your browser’s address bar, it essentially means that the data exchanged between the browser and your website is not encrypted—or is not perceived as encrypted. This warning is most frequently seen in Chrome, Firefox, and Edge, and users are often advised by these browsers to exit the site for safety reasons.
The mistaken idea is that once an SSL certificate is installed, everything should work perfectly. In theory, yes—but in practice, there are several other variables involved. Below we’ll explore various potential causes and how to troubleshoot them effectively.
1. Mixed Content: The Silent SSL Saboteur
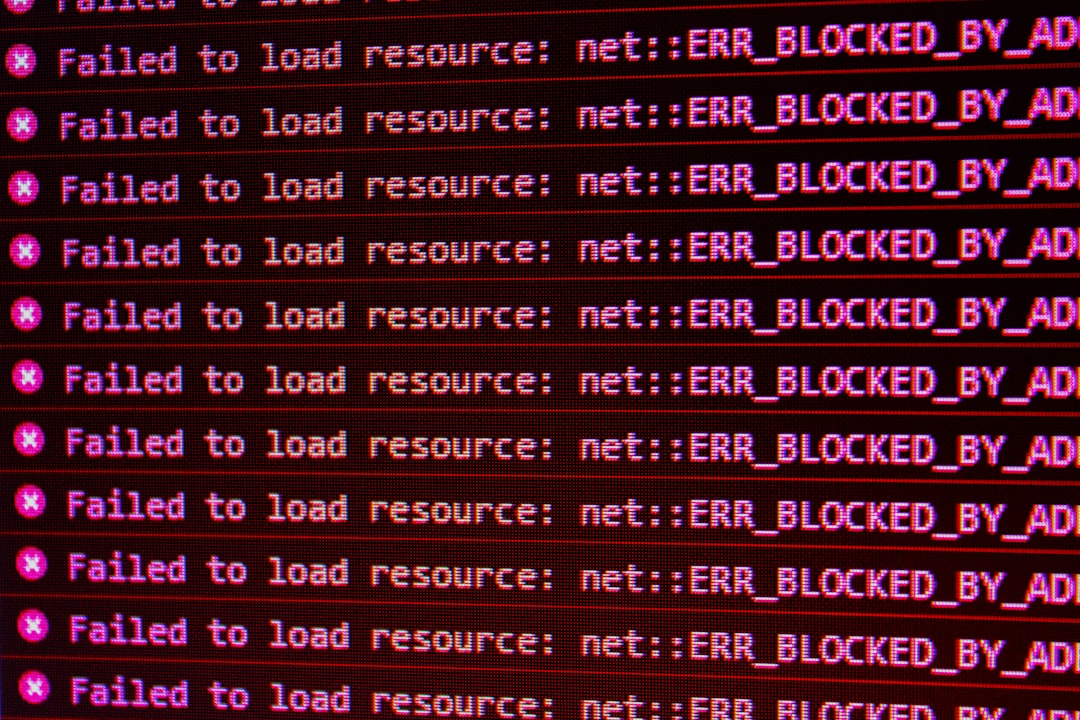
One of the most common culprits behind an insecure flag is mixed content. This occurs when a secure HTTPS webpage tries to load resources (like scripts, images, or stylesheets) over an insecure HTTP connection. As a result, browsers consider the entire page “Not Secure.”
How to Identify It:
- Use browser dev tools (press F12 or right-click → Inspect)
- Navigate to the Console tab to spot mixed content warnings
- Look for HTTP resources being called instead of HTTPS
How to Fix It:
- Update all internal links to use HTTPS
- Check plugin or theme files if you’re using a CMS like WordPress
- Use automatic update tools or plugins to replace HTTP links
If your site is peppered with old or hardcoded HTTP links, using a search-replace tool across your codebase or database can be a massive time-saver.

2. HSTS Not Configured or Misconfigured
HTTP Strict Transport Security (HSTS) is a policy mechanism that helps prevent protocol downgrade attacks and cookie hijacking. It instructs browsers to always interact with your site via HTTPS. If it’s misconfigured—or worse, missing—the browser might not enforce HTTPS properly.
Best Practices for Using HSTS:
- Add HSTS headers via your web server (Apache, Nginx, etc.)
- Configure it properly with flags like includeSubDomains and preload
- Test using online tools like securityheaders.com
It’s important to exercise caution when enabling HSTS, especially with the preload option, as mistakes can be difficult to reverse.
3. Incorrect SSL Configuration at the Server Level
Even with a valid certificate, your web server might be misconfigured. This can lead browsers to flag the site as insecure, especially if they detect weak encryption algorithms or lack of support for modern TLS versions.
What to Check:
- Ensure your server supports TLS 1.2 or higher
- Remove outdated SSL protocols like SSLv3 or TLS 1.0 and 1.1
- Use intermediate certificates correctly if required by your certificate provider
Tool Tips: Use trusted SSL testing tools such as SSL Labs’ SSL Test to analyze your configuration in depth. These tools not only tell you what’s wrong but also offer recommendations for improvement.
4. The Certificate Looks Valid, But It’s Not Trusted
Certificates might appear valid in your server configuration but may not be trusted by all browsers. This typically happens with self-signed certificates or certificates from obscure Certificate Authorities (CAs).
What Causes This:
- Use of a self-signed certificate for live sites
- An expired or revoked intermediate certificate
- The CA not being included in the browser’s trust store
How to Fix It:
- Always purchase from a trusted CA or use services like Let’s Encrypt
- Ensure full certificate chains are present on your server
- Regularly update and maintain certificates, including intermediates
To verify if the certificate is properly configured across all devices and browsers, use cross-browser SSL checkers like SSL Shopper or Why No Padlock.
5. Browser or Device Caching
Sometimes, the “Not Secure” message is just a browser being stuck in its old ways. Browsers and devices cache SSL certificate and redirect information, especially HSTS settings, which may continue to show a warning even after issues are resolved.
Steps to Refresh:
- Clear your browser’s cache and cookies
- Restart the browser or use incognito mode
- Try accessing the site from a different browser or device
In persistent cases, you may need to clear HSTS settings manually from the browser’s advanced configurations.
6. Redirect Loops or Poorly Handled Redirects
If your site is redirecting between HTTP and HTTPS repeatedly, browsers might time out or flag the page as unsafe. Poor redirect logic can also confuse crawlers and caching layers, exaggerating the problem.
Solutions:
- Update .htaccess, Nginx, or application-level settings to force HTTPS properly
- Avoid multiple redirect steps from one version of the URL to another
- Use a redirect checker tool to trace how your website handles requests
7. Content Delivery Networks (CDNs) and Caching Issues
If your site uses a CDN like Cloudflare or AWS CloudFront, the warning might stem from how HTTPS is handled between your origin server and the CDN or between the CDN and the user’s browser.
Common CDN-Related Issues:
- SSL not configured properly in the CDN dashboard
- CDN serving cached HTTP content
- Mismatch between the SSL mode (Flexible, Full, Full (Strict))
Always use Full (Strict) if your origin server has a valid certificate. This ensures end-to-end encryption.
8. Check for Site-wide HTTPS Enforcement
Simply having an SSL certificate installed doesn’t mean every visitor will land on your secure version. Users typing example.com could end up on HTTP unless you enforce a redirect to HTTPS universally.
Actions to Implement:
- Set up 301 redirects from HTTP to HTTPS at the server level
- Use canonical tags and sitemap URLs with HTTPS
- Update configurations in Google Search Console and analytics platforms
Conclusion
Seeing a “Site Not Secure” warning when your SSL certificate is valid can be alarming, but it isn’t usually a dead end. In most cases, it’s a warning sign of suboptimal configuration. Whether it’s mixed content, incorrect redirects, or CDN mismanagement, each problem has a solution.
By carefully walking through these troubleshooting steps, you can ensure that your SSL certificate is not only valid but also effective in delivering the full weight of security users expect—ultimately building trust, improving performance, and enhancing the overall credibility of your online presence.
Stay vigilant and regularly audit your website’s SSL and security settings. A few hours spent now can save your business reputation in the long run.




